DKIM signing is unavailable if you are using a re-authenticating user.
DKIM is an email authentication method designed to detect forged sender addresses in email. When signing outgoing messages with DKIM, recipients can verify a respective message is from the sender it claims to be from and that the content of the message has not been modified.
Why should I use DKIM?
There are several advantages to using DKIM to sign your outgoing emails:
- The recipient is able to verify that the message originated from the specified sender
- The recipient is able to verify that the message content (and important headers e.g. the subject) has not been altered
- It lowers the chance of the email being identified as spam, although this is not the primary reason to sign
If a spammer is trying to abuse your domain or email address, using DKIM reduces the chances of spam getting through. Many email servers check for a valid DKIM signature on incoming email.
How does it work?
DKIM adds a special DKIM Signature to the email headers. This signature contains a hashed value of the content (both important headers and the body). When a server that is checking for DKIM receives an email, it does the following:
- Retrieves the public key from the DNS of the sending domain
- Uses the key to decrypt the signature
- Verifies the content
The exact actions a mail server takes when it discovers an invalid signature depend on the configuration of that server.
What do you sign by default?
Besides the body, the following headers are by default included in the signing:
- from
- date
- subject
- reply-to
- sender
- to
- cc
- bcc
- message-id
- in-reply-to
- references
- content-type
- mime-version
- content-transfer-encoding
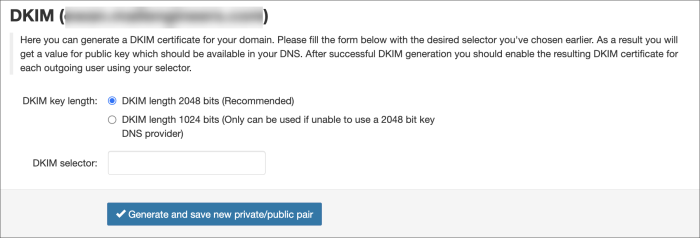
Generate a DKIM certificate in the Mail Assure Control Panel
- Login to Mail Assure to the Domain Level Control Panel
- Select Outgoing > DKIM
- Choose the DKIM key length
The recommendation is to use 2048, if your DNS accepts it
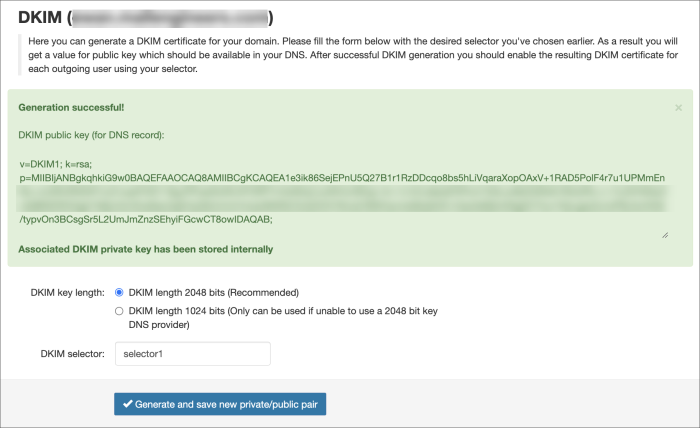
- Enter the DKIM selector and click on Generate and save new private/public pair
- Once the key has been generated, create a TXT DNS record on the hostname, for example for:
selector1._domainkey.example.invalid
Where:
selector1is what was entered into the DKIM selector field in Mail Assure_domainkeyremains as it isexample.invalidis replaced by your domain name
And enter value of this DNS record equal to the key given in the green box in Mail Assure e.g.
v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMXXXXXXcqo8bs5hLiVqaraXopOAxV+1RAD5PolF4r7u1UPMmEnBo+ncGRxRN5W7vc01yeePr5D118gJPIFaeWz0fLKFORPYr44dWqCJuWhVz/BOg/+ih+1z1kCu6pfqP3Fkvh10ALsv8bDQRsfLY62s2Rc+r+1hJlVH5KpOxQ9BNDWO2g51iMjIJ4xCSnaNavZqEHyQSUmmi/mtJa/8tNRZ/ZxQOOh76mz2/9tlKHynns58cjfeVD+OszAdMjVxWigDCYIuv1XeLqjwZcrroPBJ4o/KAS/typvOn3BCsgSr5L2UmJmZnzSEhyiFGcwCT8owIDAQAB;
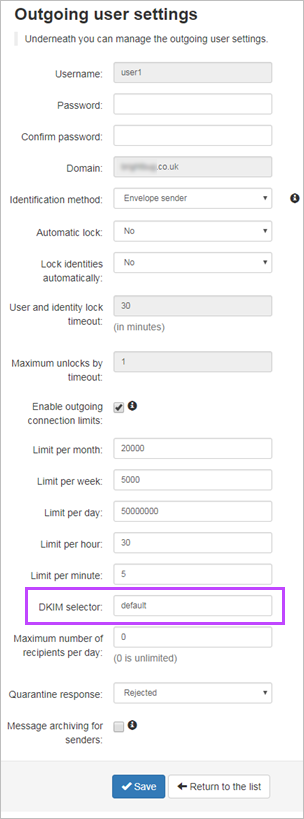
- In the Mail Assure's Outgoing > Manage Outgoing Users/Authentication page for your Outgoing User/Authentication Method (see Outgoing Users/Authentication Methods), edit this to enter what was used in step #4 in the DKIM Selector field
If you do not change the DKIM selector in the Outgoing Settings page to the one used in the DKIM key generation page, no DKIM signing will be done by the filter.
The DKIM selector can be whatever you want it to be.
Any domain that sends using outgoing authentication that has this selector, should sign with this (assuming they do not have their own DKIM).
For further information on DKIM, see http://dkim.org/info/dkim-faq.html
Further reading
The following sites provide more information on DKIM: